??Additionally, Zhou shared the hackers started out utilizing BTC and ETH mixers. Given that the title implies, mixers combine transactions which more inhibits blockchain analysts??ability to monitor the funds. Pursuing the use of mixers, these North Korean operatives are leveraging peer to look (P2P) sellers, platforms facilitating the direct invest in and offering of copyright from a person user to a different.
Threat warning: Getting, offering, and holding cryptocurrencies are activities that are issue to superior current market possibility. The unstable and unpredictable nature of the cost of cryptocurrencies may possibly cause a substantial loss.
Furthermore, it seems that the threat actors are leveraging income laundering-as-a-service, furnished by arranged crime syndicates in China and nations around the world throughout Southeast Asia. Use of the provider seeks to further more obfuscate money, lowering traceability and seemingly using a ?�flood the zone??tactic.
Whilst there are many solutions to market copyright, such as as a result of Bitcoin ATMs, peer to look exchanges, and brokerages, usually the most successful way is through a copyright exchange platform.
This may be perfect for newbies who could possibly really feel overcome by Highly developed resources and selections. - Streamline notifications by decreasing tabs and types, that has a unified alerts tab
Critical: Before beginning your verification, you should make sure you reside inside of a supported point out/location. You can Verify which states/regions are supported right here.
Besides US regulation, cooperation and collaboration?�domestically and internationally?�is critical, notably provided the restricted opportunity that exists to freeze or Get better stolen cash. Effective coordination between field actors, govt companies, and law enforcement needs to be included in any efforts to improve the security of copyright.
It boils all the way down to a source chain compromise. To perform these transfers securely, Each and every transaction calls for several signatures from copyright staff, often known as a multisignature or multisig course of action. To execute these transactions, copyright depends on Harmless Wallet , a 3rd-occasion multisig platform. Earlier in February 2025, a developer for check here Harmless Wallet fell for just a social engineering assault, and his workstation was compromised by malicious actors.
On February 21, 2025, copyright Trade copyright executed what was designed to certainly be a routine transfer of user funds from their chilly wallet, a safer offline wallet employed for lasting storage, for their heat wallet, a web-linked wallet that gives extra accessibility than chilly wallets when retaining additional protection than incredibly hot wallets.}
 Ralph Macchio Then & Now!
Ralph Macchio Then & Now!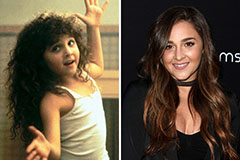 Alisan Porter Then & Now!
Alisan Porter Then & Now! Susan Dey Then & Now!
Susan Dey Then & Now!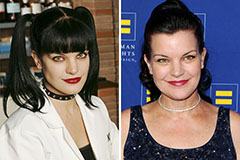 Pauley Perrette Then & Now!
Pauley Perrette Then & Now!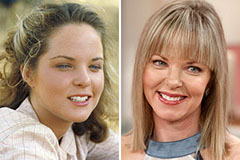 Melissa Sue Anderson Then & Now!
Melissa Sue Anderson Then & Now!